Synergizing security, generative AI, and data on AWS – Workshop takeaway
Yesterday, I attended this workshop on Synergizing security, generative AI, and data on AWS.
It covers 3 main topics:
- Cost optimization
- Security optimization
- GenAI and data analytics
Also, it comes with 2 pretty fast workshops: 1. Service Screener, 2. AWS Quicksight and Amazon Q.
We all know that AWS has hundreds of services it is even hard for their Solution Architect to keep track of what is new. Some of those that shared slip past most of our radar and can be tremendously useful but didn’t get much visibility.
So sit back, it will be a long story.
PS: I’ll skip all the well-known common tools and just focus on those that did not get popularized.
Cost optimization
Managing cost and budget with Amazon Q
You probably gonna hear a lot about Amazon Q. Here is a brief intro to Amazon Q.
Amazon Q is a chatbot developed by Amazon for enterprise use.
In short, treat it like a ChatGPT within the AWS for you to ask questions. In this case, AWS has embedded Amazon Q as part of the Cost Explorer. You can start to ask questions about certain billing directly within your console.
Cost Optimization Hub
This service seems too good to be true honestly. Comes at no cost. Rather the opposite helps you to save even more cost.
Here is a list of some optimization opportunities we can take:
- Stop idle or unused resources
- Rightsizing within the same CPU architecture — AWS Compute Optimizer
- Upgrade (eg. moving EBS gp2 volume to gp3 volume)
- Migrating to AWS Graviton — arm-based instances that are cheaper to operate with better performance.
- Purchase of saving plans or reserve instance
- Deduplication across related recommendation
Let me give an example. Say, you’re using EC2 to host. How sure are you that using m2.large is the most optimal for your infra? That’s where this service comes. It tracks your running workload, maybe for about a month, then provides recommendations for saving.
Some simple optimization right off the bat could even be changing from gp2 to gp3 EBS, or even recommending AWS Graviton — arm-based instances that are cheaper to operate with better performance.
Consolidating account
To be honest, this is something we are so used to it regularly that we take it for granted. Some advantages of having a master account can help to share reserve/saving plan resources, bulk discounts for hitting tiering, and access to restricted credits.
Cost Anomaly Detection
Nuff said the title says for itself.
AWS Optimization and Licensing Assessment
If you’re using proprietary stuff like Microsoft or Oracle. You need this.
Discover the best path to cloud migration and cost reduction with the AWS Optimization and Licensing Assessment (AWS OLA) by analyzing actual resource use, third-party licensing, and application dependencies with an AWS OLA.
Making use of Cloudfront
After so many years of using AWS, one of the uncontrollable costs is data transfer. We just have to take what is billed to us. Well, we can do more.
Cost with and without Cloudfront is as follows: {{Find the info}}
Also, take advantage of the bigger free tiering resource. EC2 Data Transfer (Free tier – 100GB) vs CloudFront Data Transfer (Free tier – 1TB)
Autoscaling
I think generally, we all know how can this help to improve reliability and also save cost. Just to recap, 4 types of auto-scaling – simple step, target tracking, schedule scaling, and predictive scaling.
Maintaining hygiene
Archiving or deleting unused resources as needed, eg. S3, EFS, EBS, CloudWatch log, etc. Make sure to understand our Data retention policy and configure it accordingly.
Security Optimization
Next up, is security which focuses on the well-architected framework
IAM
IAM Access Analyser
Starting with this analyzer. Something that we have stuck for quite some time to scale our access operation while maintaining the PoLP. This tool says it all.
How it works is by granting access to people to do a job. Then, use the analyzer to see the permission that was used over a certain time.
Some other features that this service offers are:
- Simplifying inspecting unused access
- Monitoring AWS accounts continuously for unused access
- Review external and unused access findings centrally and prioritize accounts.
Detection
AWS Cloud Trail, AWS Guard Duty, AWS Inspector, AWS Security Hub
Nuff said. These services here are all quite well-known if you’re into the security space already.
Infrastructure Protection
AWS Shield
DDoS protection is available at no additional cost. By default, it already protects against common attacks like SYN/UDP floods, reflection attacks, etc.
Whereas the paid Advanced Shield offers DDOS Response Team, cost protection, and Layer 7 protection. Which I think is useful in case DDoS does happen, we are protected.
Layer 7 protection offers managed, elastic, and integrated WAF. Those rules are managed by AWS and some other custom rules are provided by other partners.
AWS CloudFront Unified Security Dashboard
With this, you can get a pretty interesting holistic view of what is happening within your application traffic direction. The best part is, that you can even block traffic within the console.
Is Accessible from CloudFront and AWS WAF console, by providing high-level visibility into top rules and contributors. Coupled with some built-in dashboards for Fraud Control and Bot Control activities.
Data Protection
AWS Macie
The good old Macie, which we all hardly pay attention to these days.
Incident Response
AWS Trusted Advisor
Did mention this tool in this category, but I am not sure how this is related. Anyway, is best to establish a good runbook, process, and policy within the company to ensure that response can be automated.
Wrapping up with a workshop
Introduce Service Screener. All the mentioned best practice is coded into this script which generates the report for the AWS environment. Pretty straightforward and safe to use, since is open-sourced and community-driven. Just follow the README, should be good to go.
The workshop has provided a sample AWS environment for us to use. Nevertheless, the report is quite straightforward to read.
Launch CloudShell and install the screener with the following script.
python3 -m venv .
source bin/activate
rm -rf service-screner-v2
git clone https://github.com/aws-samples/service-screener-v2.git
cd service-screener-v2
pip install -r requirements.txt
alias screener="python3 $(pwd)/main.py"run screener --region us-east-1
Click on Actions, then Download file. Paste the zip path~/service-screener/output.zip
Have fun exploring the index.html!
Data in AWS
Amazon S3 as the centralized data lake
For many good reasons, it is cheap, durable, reliable, and scalable. It also provides extensive capability to store and retrieve data that cater to most of the compliance needs.
Therefore, is one of the most used analytics tools in AWS.
- Mapping data processes to a service
- Data warehousing: Amazon Redshift
- Query: Amazon Athena
- Big data processing: Amazon EMR
- Log and search analytics: Amazon Open Search Service
- Real-time analytics: Amazon Kinesis & Amazon MSK
- Visualization: Amazon QuickSight
Bring ML closer to the data
Simply put it, is just another tool with an ML suffix. Eg. Amazon Aurora ML, Neptune ML, RedShift ML, Athena ML
Generative AI application
To build any generative AI stuff. If the goal is to offer some meaningful differentiation, we need to start with the data. These come with a few considerations to take note of:
- Storage: structured and unstructured data
- Database: SQL, NoSQL, document, graph, vector
- Analytics: Search, streaming, batch, interactive
- Integration: Capture, transformation, streaming
- Governance: Catalog, quality, privacy, access control
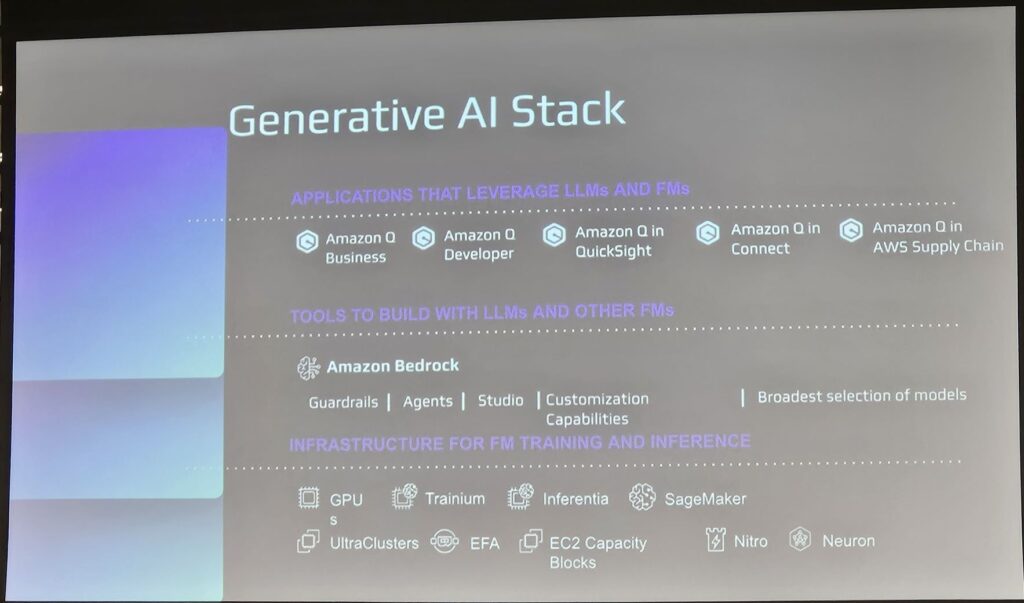
Generative AI Stack
The stack we are looking at
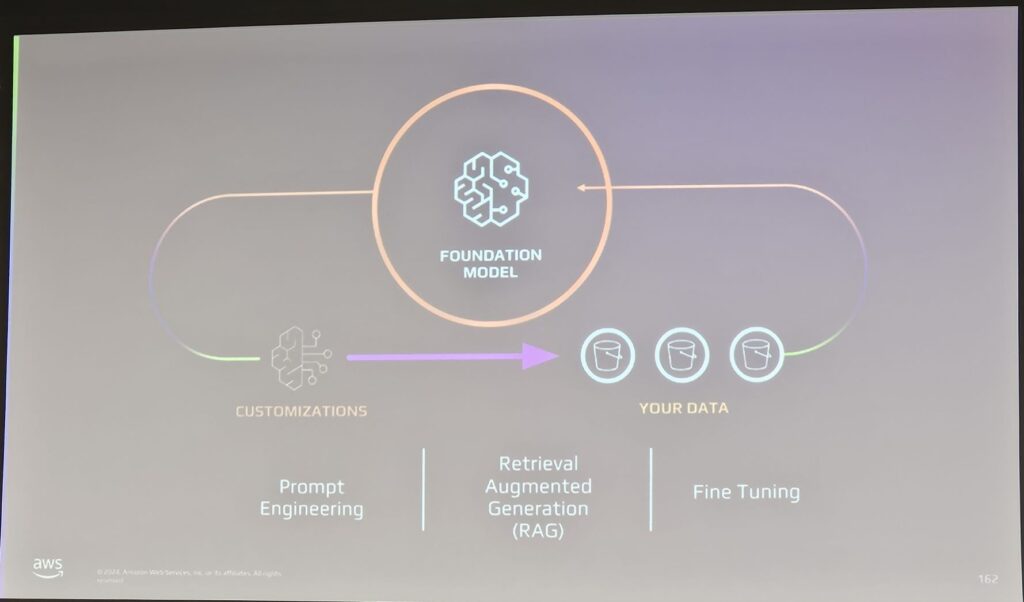
The general flow works like this:
Building Knowledge Bases with Amazon Bedrock
- Securely connect FMs to data sources for RAG
- Fully managed RAG workflow including ingestion, retrieval, and augmentation.
- Built-in session and context management for multiturn conversations
Establishing Guardrails with Amazon Bedrock
We also want to implement safeguards to our application and align with a responsible AI policy. This tool covers it as well. It comes with some build features to:
- evaluate prompts and model responses
- configure thresholds to filter harmful content, jailbreaks, and prompt injection.
- defining and disallowing denied topic
- remove PII and sensitive information
- filter hallucination
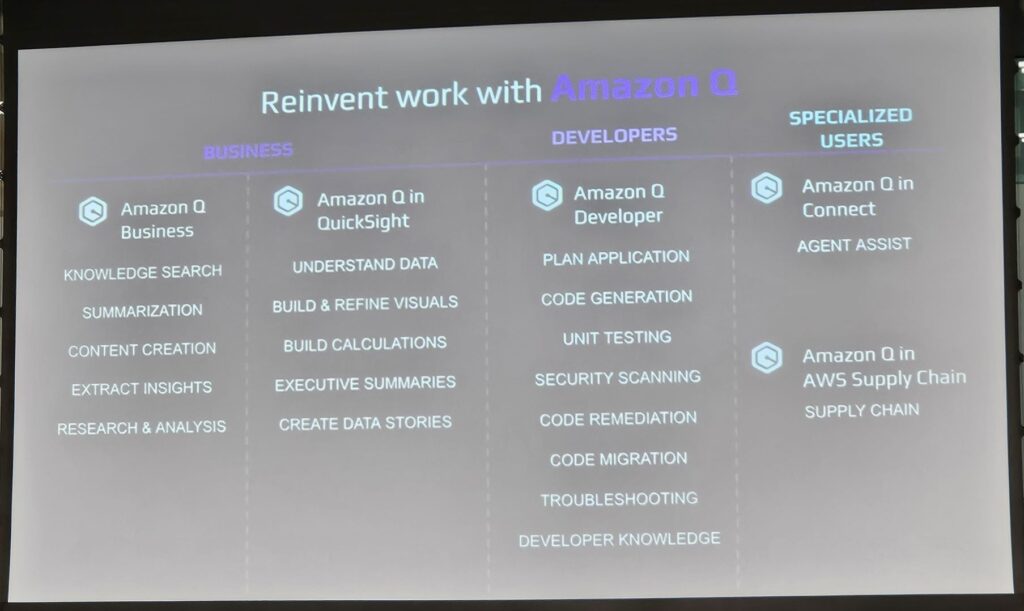
Amazon Q
This is where the main meat of the talk is. Which is to introduce the power of AI in the existing AWS environment. Do you know that you can easily access Amazon Q by using this button at no cost?

Amazon Q is powered by Bedrock almost everywhere within AWS.
Ending with another workshop
To build a QuickSight dashboard with just Amazon Q. Surprise that building a dashboard can be so much fun, just putting in the query.
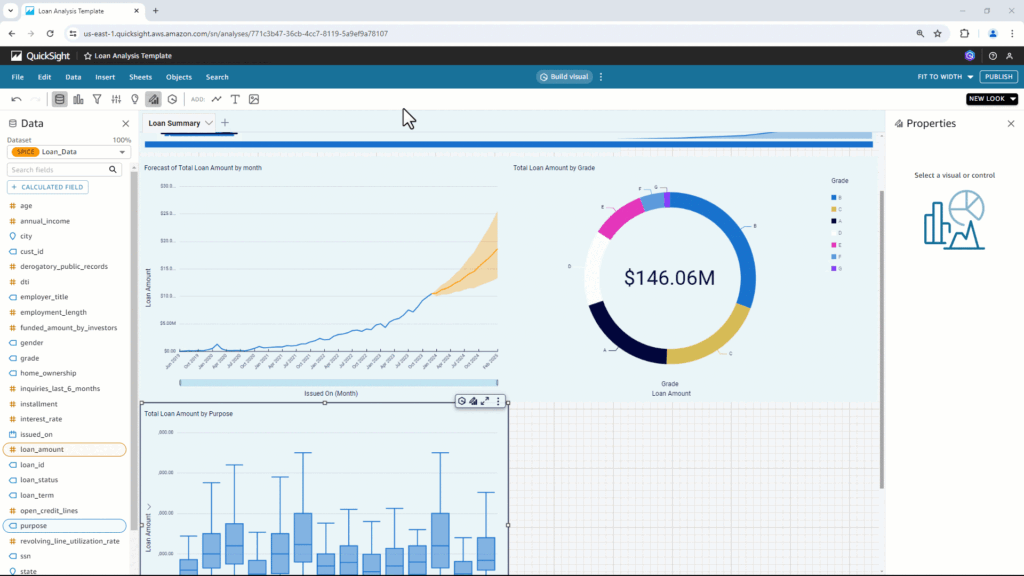
Adding charts into QuickSight with Amazon Q by giving a prompt of what you want.
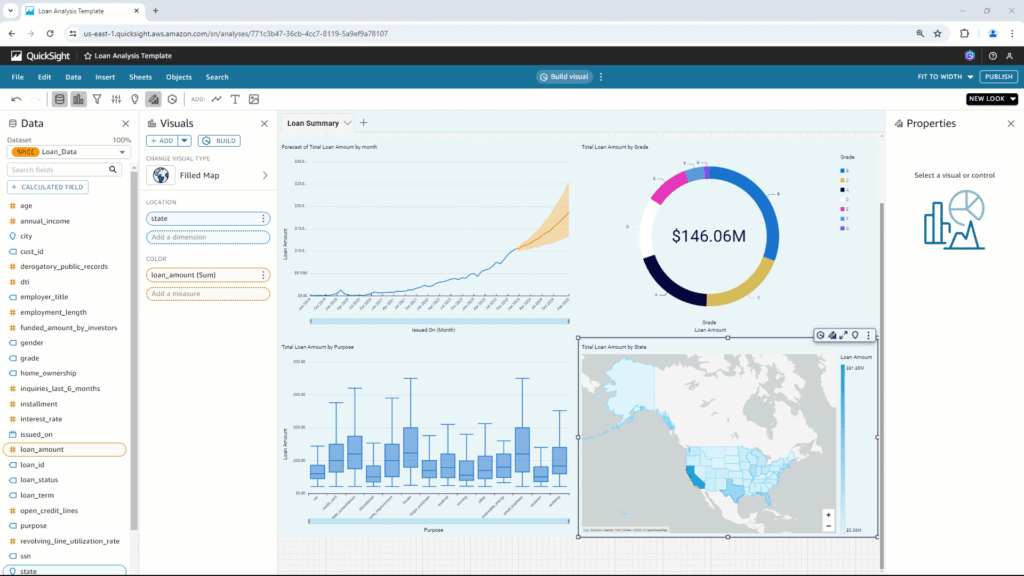
Edit the charts with prompt
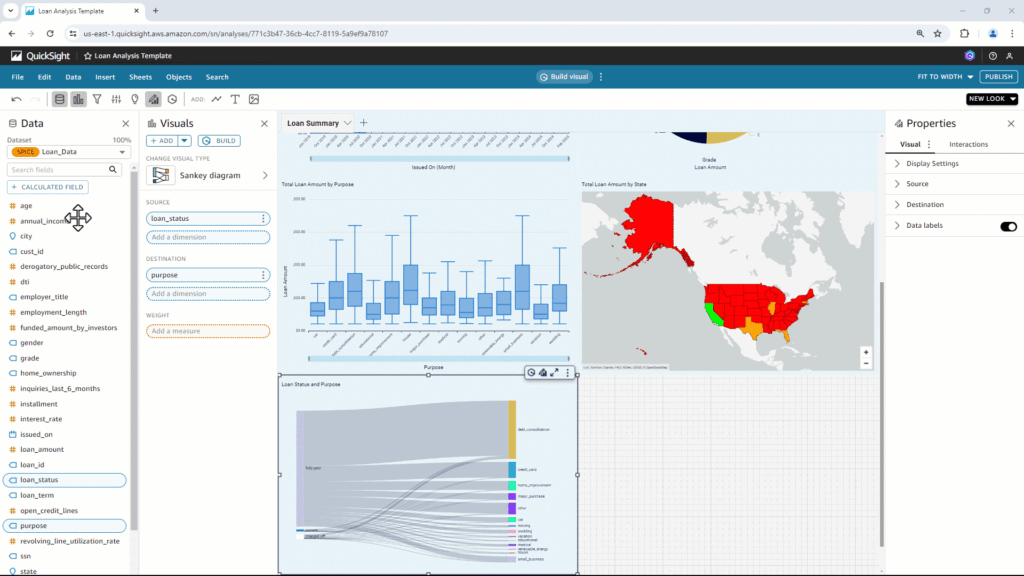
Handling calculated field. For words that the Q doesn’t understand
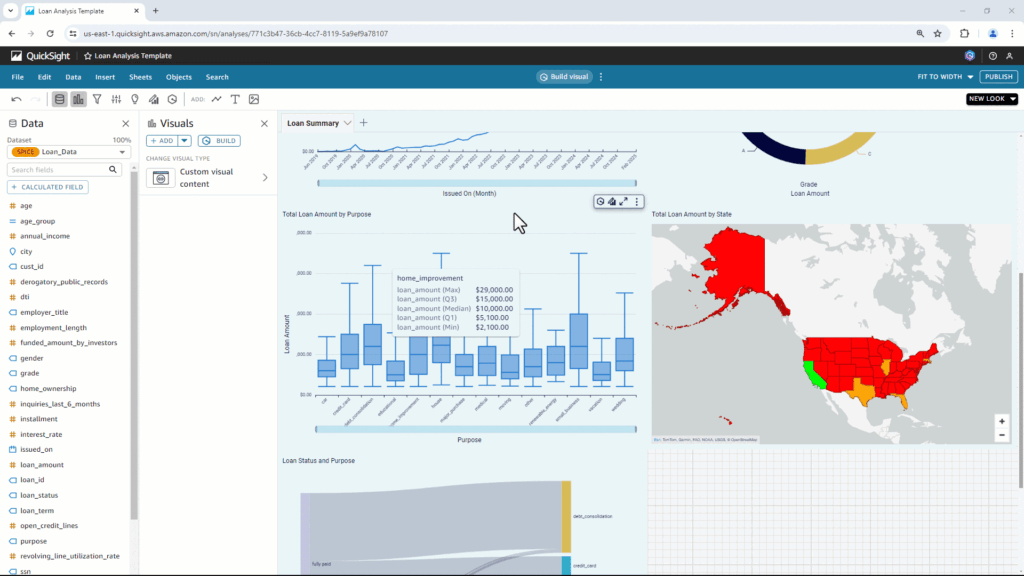
Now, you can prompt works like by “age group”
Kudos to you if you have read until so far. Give a ”wow” if you like me to do a recording run-through of all the new tools they introduced.